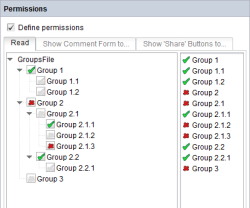
Evaluating user permissions
The evaluation of the user permissions (right-hand area) in conjunction with the group hierarchy (left-hand area) is not insignificant and must therefore be explained in greater detail using an example:
Access is basically prohibited for everyone “![]() docu”. This means this is the default value for all groups for which nothing else is defined (e.g., “
docu”. This means this is the default value for all groups for which nothing else is defined (e.g., “![]() Group 3”) – therefore, if a new group is added at the highest level, “prohibited” applies.
Group 3”) – therefore, if a new group is added at the highest level, “prohibited” applies.
“Group 1” has an explicit permission through “![]() Group 1”, which also has an effect on subgroups 1.1 and 1.2 by default. If a new group is added to this level, access is allowed by default.
Group 1”, which also has an effect on subgroups 1.1 and 1.2 by default. If a new group is added to this level, access is allowed by default.
“Group 2” is also configured – in this case with “![]() everyone prohibited”. This has an effect on 2.1 and in 2.2 is explicitly “
everyone prohibited”. This has an effect on 2.1 and in 2.2 is explicitly “![]() allowed” again by default. The permission in 2.2 has an implicit effect on 2.2.1. Therefore, all members of 2.2 are authorized. In node 2.1 access is differentiated still further: Here “Group 2.1.1” is explicitly allowed while “Group 2.1.3” is explicitly prohibited. No specification is made for “Group 2.1.2”, the value therefore depends on the first explicitly configured parent (here: “Group 2”).
allowed” again by default. The permission in 2.2 has an implicit effect on 2.2.1. Therefore, all members of 2.2 are authorized. In node 2.1 access is differentiated still further: Here “Group 2.1.1” is explicitly allowed while “Group 2.1.3” is explicitly prohibited. No specification is made for “Group 2.1.2”, the value therefore depends on the first explicitly configured parent (here: “Group 2”).
Therefore, if “Group 2” is reconfigured from ![]() to
to ![]() , “
, “![]() Group 2.1.2” changes to “
Group 2.1.2” changes to “![]() Group 2.1.2” (note: this also applies, of course, to “Group 2.1” but not to “Group 2.1.1” or “Group 2.1.3”). Effectively, this configuration means that people who are only in “Group 2” do not have any access and people who are in 2.2 or in one of its subgroups or in 2.2.1 are given access. People in groups 2.1.2 and 2.1.3 are still refused access. Those in 2.1.3 are even still refused access if 2 is reconfigured to
Group 2.1.2” (note: this also applies, of course, to “Group 2.1” but not to “Group 2.1.1” or “Group 2.1.3”). Effectively, this configuration means that people who are only in “Group 2” do not have any access and people who are in 2.2 or in one of its subgroups or in 2.2.1 are given access. People in groups 2.1.2 and 2.1.3 are still refused access. Those in 2.1.3 are even still refused access if 2 is reconfigured to ![]() .
.
The evaluation of the authorization configuration is displayed on the right-hand side of the input component. The calculation involves the complete group tree being run through and the evaluation for each node is inserted in an “allowed” or in a “prohibited” list. The prerequisite for this is that default assignment takes place at the root level (i.e., “docu”).
In general a distinction is made between nodes on which permissions have been explicitly defined and nodes on which no permissions have been defined. If permissions have not been defined on a node, the permissions of the parent node apply. If the parent node does not have any defined permissions either, the permissions of the first higher-level node for which permissions have been explicitly defined are adopted. If permissions are not defined in any node, the value ![]() is used as a default for all nodes.
is used as a default for all nodes.